Beware of this dirty trick to get past two-factor authentication
As Internet security tightens, with more ways to safely log into multiple services, from multiple devices, one weak spot remains available to hackers to exploit: the human element.
Social engineering is an old term, popularized by early hackers, who once gained frequent access into telephone systems, government and corporate intranets, during a time in which users enjoyed a much younger, simpler Internet than what we know, and take for granted, today.
Two-factor authentication is one of the several responses to the fragile nature of passwords, across all systems, from social media sites, to corporate, banking and government applications. For most security experts and hackers, getting around a password system is somewhere between child’s play, and target practice, which makes it merely a matter of time to gain access to any system where a login/password prompt is all that stands between a hacker and any kind of concealed information within that system.
When two-factor authentication is enabled, logging into a website, may that be a social media network, a banking website, or a corporate resource for employees of a company, will trigger a code sent to a mobile phone number, which is required right after entering the regular password. Without that code, access won’t be granted, which means that without access to the physical phone of the owner of the account, there is no way to gain access to a two-factor authentication-protected account online. This eliminates the worry of hackers gathering login information from a stolen Windows laptop or tablet PC.
With that being said, hackers are catching on, and have developed their own ways around two-factor authentication, using the only weapon at their disposal: human error.
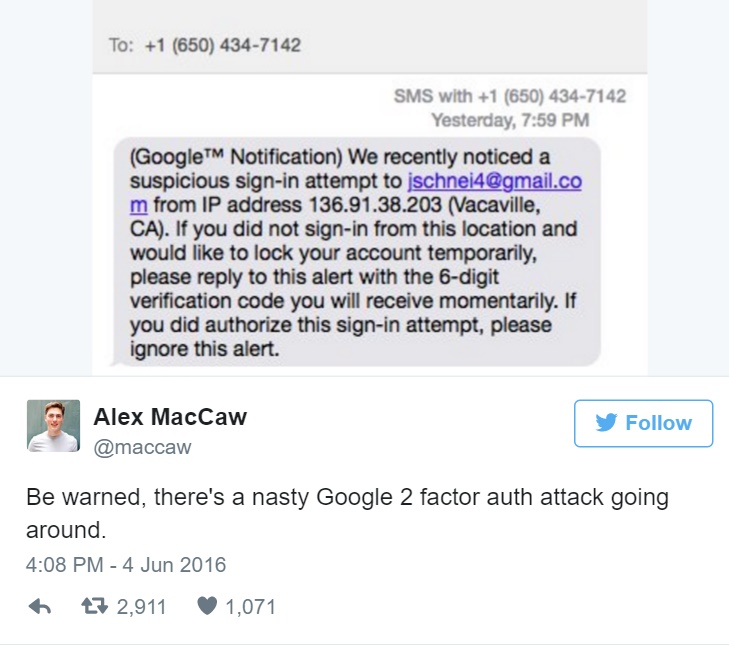
Humans are a lot easier to hack than machines, and a recent attempt to use social engineering to get past two-factor authentication, has been spotted on Twitter, by user Alex McCaw ( @maccaw), who has published a screenshot of a text message from a hacker, impersonating an automated Google notification system.
The message drew attention, as it contained detailed information, including the email of the user, the IP address, the geographical location, as well as a notice urging the user to text back a 6-digit verification code to the hacker’s phone number.
Two-factor authentication hack - deconstructed
There are three main components to take into account, that make this hack possible:
first of all, the originating number of the attacker can be spoofed to appear to be a local number, when in fact the hacker could be located anywhere in the world, while still retaining the ability to send and receive text messages using a VoIP service.
Secondly, all information about the user can be easily gathered through automated web search algorithms written to follow patterns like phone numbers, email addresses, and other information. For instance, one such program may use an algorithm that will search every instance of a public record on which both a certain email address and a phone number are both present.
Based on that assumption, the third component of this hack is the assumption that the user’s phone number is also the one used in two-factor authentication, at which point the hacker will feed this information to an automated software, which will send out thousands of text messages, while at the same time triggering thousands of two-factor authentication logins, and wait for responses.
What to do if you get a suspicious text message regarding two-factor authentication
No legitimate online service will ever ask a user to email or text a password, or any kind of login information. This is also true for two-factor authentication, which is why if you receive a text message asking you to text back a code, password, PIN number or any other information required to log into a system: it’s a scam.
The beauty of an automated system is that it doesn’t need you to tell it who you are, because it already knows that, which makes the need to provide passwords or other login information, redundant, and dangerous, as that information could will be intercepted.
The third step
Two-step authentication via text message is still leaps and bounds ahead of any password-based security available, still it’s not an air-tight system, as it is still vulnerable, to some degree, to social engineering. This is why Google and Microsoft have developed systems where text messages are not even necessary.
Google’s way to eliminate the need to use text messages for verification, comes in the form of Google Authenticator, which is an app that generated authorization codes every 60 seconds, automatically, without the need to communicate with any text-messaging service.
Microsoft has a similar system for its users to log into its services, with the Microsoft Account app, which presents the user with an Approve/Reject prompt, along with a verification code, upon a login attempt, with no need for any text-message communication.
Both apps are available across all platforms, including android and iOS, which makes it very convenient for users to authorize access to services, using devices that must be physically accessed and unlocked, some of which use biometric authentication like face recognition of fingerprint readers, closing the loop to hackers looking to dupe users into revealing login information through direct contact.