Microsoft is working on finalizing new security features for Windows 10 Enterprise customers
The Enterprise edition of Microsoft Windows 10 will soon integrate some important security enhancements, much anticipated by business customers.
Future updates of Windows 10 Enterprise edition will allow organizations to manage Windows PCs, tablets, smartphones, and any other device running Windows 10, with a very granular degree of control and security.
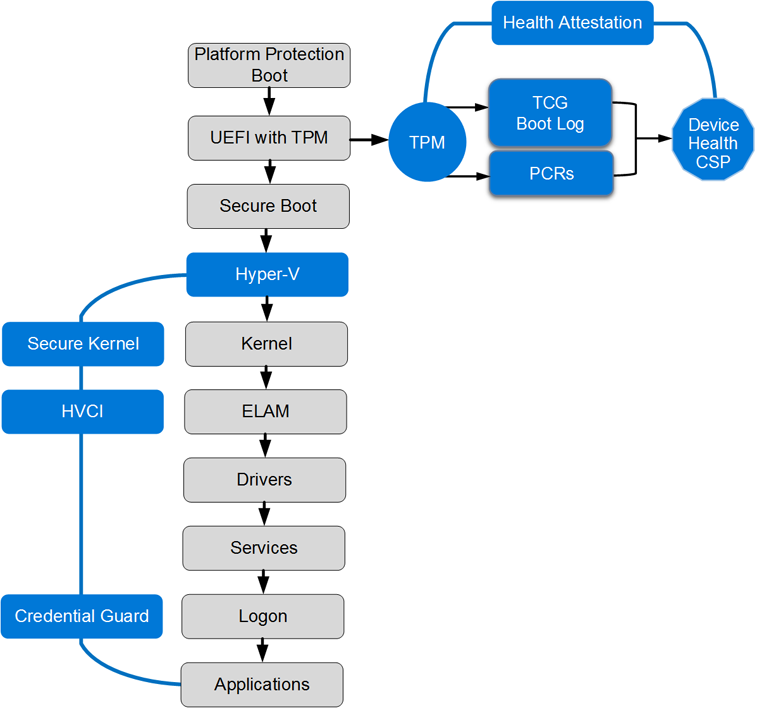
Device Guard is one of the two main features that will be implemented down the line, and it allows organizations to lock Windows 10 devices, to ensure they run only a predefined list of trusted apps, may those be desktop apps or universal apps from the Windows Store.
Device Guard not only prevents unauthorized apps to be installed and run on devices, but also other apps that may try to install themselves through browser activity, which is a scenario that has already been contemplated by Microsoft, in reference to the sandbox properties of the Edge browser.
At the core of Device Guard, is a hardware-based isolation and virtualization, using Hyper-V Code Integrity Service, which protects the system from zero-day exploits and vulnerabilities.
Credential Guard is the second major security enhancement to be introduced to Enterprise customers. The feature is designed to protect Windows credentials by generating access tokens each time a successful login is detected. The credentials are then stored in a virtualized environment, away from the Windows 10 kernel. This means that if a system is compromised, credential information will still unavailable to intruders. Most importantly, if a machine is compromised, the damage will not spread to other machines on the same network.
Managing Credential Guard will be possible through Group Policy, to keep the procedure simple to those already familiar with existing administration interfaces. Other methods of issuing Credential Guards certificates and policy settings will also be available as PowerShell scripts.