Cyber-criminals go corporate with RaaS (Ransomware as a Service), and this is why you should be worried.

Ransomware is a rampant plague and a cyber-security nightmare that won’t go away anytime soon. Ransomware is also an 18 million dollar a year business, according to 2015 reports with an average paid ransom between $300-$600.
Earlier this year, a team of researchers from the University of Florida, began working on a counter-attack to ransomware, with promising reports of an average of 10 sacrificial files for each circumvented attack by a different family of ransomware. As good a news as it sounds, we are still a ways from mainstream adoption of a solution that is still under heavy testing and still waiting for further funding and endorsement by larger cyber-security vendors.
In the meantime, the responsibility lies with the user to be wary of suspicious activity on the systems they work on day in and day out.
How bad is it?
Very. Ransomware authors are the true “men in black” of the operation, and have constructed a “corporate style” affiliate network where criminals who lack the skills to create ransomware, can buy it “to order”, and deploy it. Each ransom that is paid is split between the original author of the ransomware, and the “script kiddie” (an old-fashion term to describe wannabe-hackers with enough computer skills to execute programs they know nothing about, and brag about it).
How does it work, and why don’t they get caught?
The author’s “cut” in the operation can vary between 5% and 25%, depending on the targets, and the depth of the attack. Both author and “affiliate” carry out their operations from what the media have come to refer as the “Dark Web”, or the “Deep Web”, depending on how dramatic one wishes to sound to their peers.
Dark/Deep Web is an erroneous and gross oversimplification as there is no such thing as a sublayer of the Internet, beyond the Internet itself.
In reality, things are a lot simpler than the cinematic ways they are often described:
The Internet you know is made of websites that originate from well-known locations, like GoDaddy, or a web server running from somebody’s house or office, which is surprisingly easy to set up, provided a basic knowledge of the Internet. If you know how to change the proxy settings in your browser, that’s a good start.
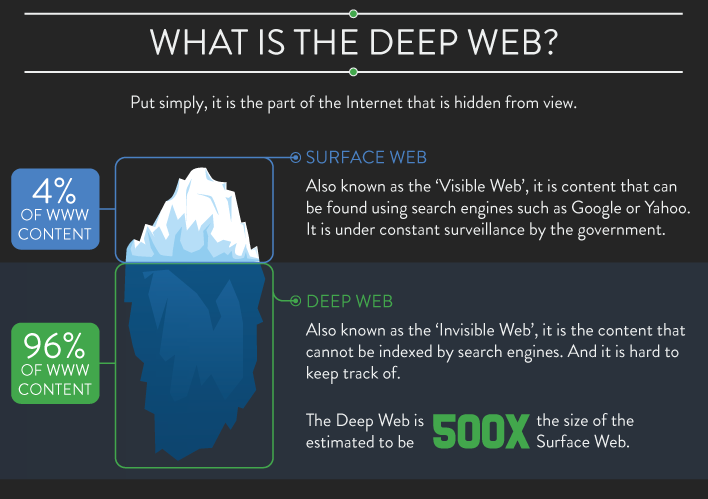
All these locations are public, as they should, because that’s how Google and other search engines are able to find them. Websites are often submitted to search engines manually, added to directories like Moz.org, or simply found by search engine bots. It is actually harder to stay hidden in the public Web, and, paradoxically, that is why it is hard to be found. The massive amount of websites creates mass competition and the need for SEO services to shift the odds of a website to be found on top of the pile.
The “Dark Web” works in the opposite way. Websites in the “Dark Web” come from spoofed locations that broadcast using encrypted protocols, such as Tor or I2P (the protocol used to obfuscate activities from the infamous “Silk Road”).
There is little structural difference between “Deep Web” websites and regular ones, except that meta-data is non-existent, which means that any information that is typical of a regular website, like description, keywords, title, and various kinds of microformats, are regarded as a liability, because they are breadcrumbs to law enforcement agencies.
The way to keep the activity on these websites hidden is to access them by using a web browser that supports any number of encrypted and spoofed networks, like Tor. Tor works by taking your IP address and bouncing your request around thousands of other IP addresses around the world, making it look like you are using somebody else’s computer.
Deeper in the dark
Because the “Dark Web” is not indexed, and there is no search engine available to simply “look for stuff”, criminals rely on direct communication, “word of mouth” and encrypted chat rooms, to find information.
There are also “well-known” wiki sites that list addresses where to find a tiny fraction what has been estimated as 500 times the amount of websites that exist in the visible spectrum of the World Wide Web. Trying to “look” for anything of value in the “Deep Web” is essentially equal to rocket in outer space hoping to bump into Crypton.
Once “inside”, (meaning: once a large amount of Bitcoins is paid for extremely disposable information), a “business” relationship can be created with authors of various kinds of malware, from simple spyware, to the nastiest, most virulent form of ransomware. Everything can be had for the right price. Ever wonder what happens when your credit card is cloned or stolen? This is where it ends up.
The simple reason why ransomware is so hard to fight, is because the true suppliers stay hidden, and are protected by hordes of “affiliates” who make a lot of money from this 18-million-dollars-per-year “industry”. In a sense, Ransomware as a Service, is not unlike a software-based drug cartel, that thrives because everyone, except those outside of it, get what they want, while unwitting users and businesses suffer. The only “upside”, if we can call it that, is that no guns are involved. It’s a “clean-cut”, “white-collar” crime with a high level of emotional detachment, and an almost insignificant chance for repercussions, because most perpetrators are either well outside the jurisdiction of local law enforcement, or simply because they are “cozying it up” behind layers of spoofed IP addresses and silence.
Ready to shop?
PortableOne has the best deals on Windows 10 Pro laptops, featuring the latest hardware-based security features, and full BitLocker encryption to protect your files from prying eyes.